What is Network Security ?
Protection of Information Assets to ensure Confidentiality , Integrity and Availability
What are the Objectives of Network Security ?
Confidentiality : No Data or Information is made available to any Person within or outside the organisation , other than the persons who are authorized to use that data
Integrity: No Data/Information or program shall be allowed to be modified by anyone without proper authority
Availability : All Information systems including Hardware , Communication Networks, software applications and the data they hold , is available to authorised users to carry out business activities
What are the Threats to Network Security ?
While the internet links people together , it provides endless opportunities to to criminals seeking to exploit the vulnerabilities of network of other users. These are called cyber crimes. These types of crime are hard to solve and occur without the victim ever knowing anything illegal has taken place.
- Information Gathering by attackers through port scan,social engineering,malware like virus and worms
- Attackers can exploit the communication system vulnerabilities by microwave signal tapping, optical fiber,Zombies and Botnet, satellite signal tapping, wiretapping, eavesdropping etc.
- use of protocol flaws by attackers e.g FTTP transmit communication including user ID and Password in plain text.
- Attackers may use impersonation techniques e.g spoofing and masquerading,guessing of common passwords ,session Hijacking,Man in the Middle attack
- Attackers can track your message confidentiality through traffic analysis ,temporary buffers in switches, routers , mis-dilvery of message due to congestion.
- Attackers can also change your messages , redirect the message, destroy or delete the message through use of trojan horse, Active wiretap, impersonation etc.
- Attackers can use the code downloaded and executed in the browser of the client from websites.
- Attacker can use the denial of service attack which results into loss of network availability
- Attackers can exploit cookies, scripts and active/mobile code
- Attackers can also use malicious codes e.g viruses, worms, logic bombs, mobile active x
- Attackers can also exploit application vulnerabilities by SQL injection,Cross site Scripting,cross site request forgery
- Attackers can also use Advance persistent threat to send the malware to the victim computers . This malware sends small bit of information from the system to the attacker
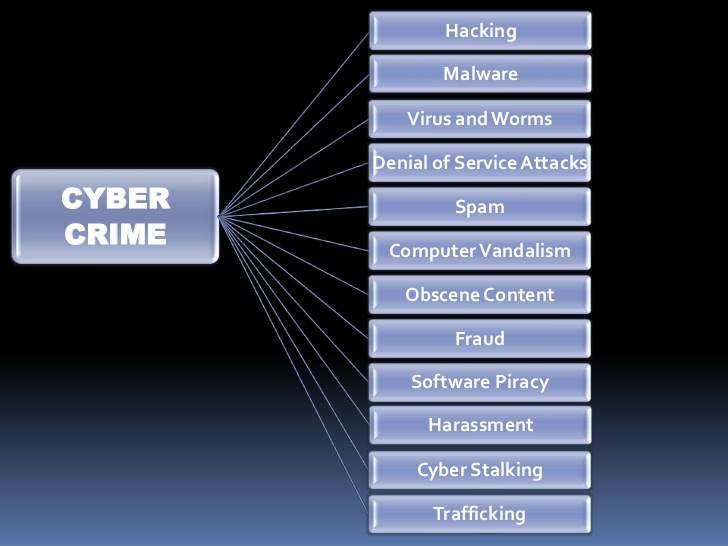
What is Cyber Crime ?
Cyber crime encompasses any criminal act / unlawful activity dealing with computers and networks (called hacking). Additionally, cyber crime also includes traditional crimes conducted through the Internet.
For example; hate crimes, telemarketing and Internet fraud, identity theft, and credit card account thefts are considered to be cyber crimes when the illegal activities are committed through the use of a computer and the Internet
What the policies to be framed to ensure network Security for the organisation ?
Make the following security policies for the Organisation
1. Data Classification and Privacy Policies
2. Acceptable use of Information Assets Policy
3. Physical Access Security Policy
4. Asset Management policy
5. Business Continuity Management Policy
6. Network Security Policy
7. Password Policy
How to Classify the Information for network Security ?
1. Data Classification
2. Classification of Assets other than Data
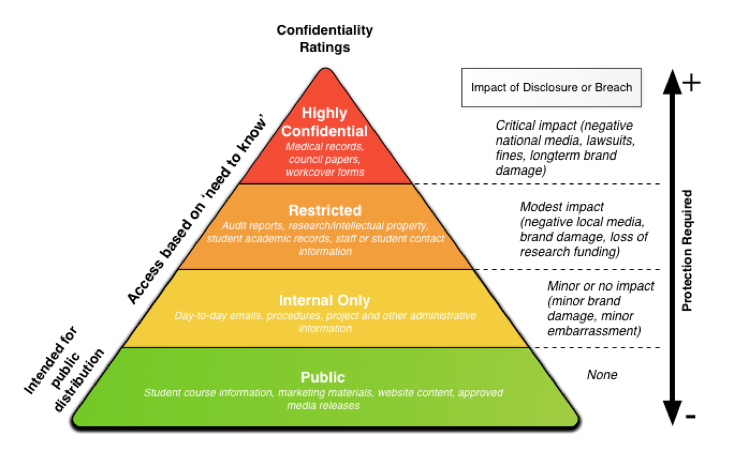
How to Classify the data of the Company to ensure network Security?
- Information for Public Purposes (No Protection required)
- Information for Internal Purposes of the company (Minor protection required)
- Restricted Information (Modest Protection required)
- Highly Confidential or Top Secret (Critical Protection required)
What is classification of Assets other than Data ?
There are numerous IT Assets for which protection is required some of them are listed below :-
1. Servers
2.Workstations
3.Portable Devices
4.Printers
5.Network Devices
6. Unattended Equipment’s e.g ATM
without security guard by Banks
How to ensure Physical protection of Information Technology Assets ?
Following are the examples of some of the Physical Security control to protect IT Assets
1.Security Guards
2.Dogs
3.Lighting
4. Deadman Door
5.Bolting Door Locks
6.Cipher Locks
7.Electronic Door Locks
8. Biometric Door Locks
9.Video Camera
10.Alarm System
11.Electronic Logging by Swip of Card
12.Manual Logging by signing visitor log
How to protect IT Assets from the environmental risk e.g fire etc ?
Following are the Environment to protect the IT assets:-
1.Selecting and Designing a Safe Site
2.Facilities Planning (power, lights etc)
3.Training to staff
4.Power Supplies
5.Ventilation
6.Fire Resistant walls, floors, ceiling
7.Smoke Detectors
8.Water Dedectors
9.Fire suppression system
10. Fire Alarm
Why we need logical access controls ?
To Protect attacks from :-
a) Masquerading : Attacker pretends to be an authorised user of system
b)Social Engineering
1.Phishing :user receive a link (appears real) on mail to provide information e.g banks ID,Password etc
2.Key Logger:Attacker install software to caputre key sequence used by user including login information
3.Malware
4.Virus
5.Worms
What are the Logical Access Controls ?
1. User Registration
2. User Access Management
3. Password Management
4. Review of User Access Rights
5. Segregation of Duties
6.Segregation of Networks
7.Network Connection and Routing control
8.Monitoring use of System
9.Database Access Control
10.Operating System Access Control
11. System configuration
How to protect the IT system from virus /Malicious codes ?
Following are the ways :-
- Installation of Anti Virus :
- Virus signatures should be updated regularly after installation
- Alters from Anti Virus are reviewed regularly for root cause
- schedule scan are regularly performed
- Continuous Training and Awareness of users
- Removable devices (PAN drives etc ) should be scanned before use
- Mail attachments from unknown sources should be handled with care
- Do not open insecure websites or links
- use separate Segments for each functions e.g separate segments for web server , authentication server ,applications and database server
- Avoid Single Point of Failure of any IT equipment
- use cryptography /Encryption
- Use firewalls
- use Intrusion Deduction system